First Class Info About How To Detect A Ddos

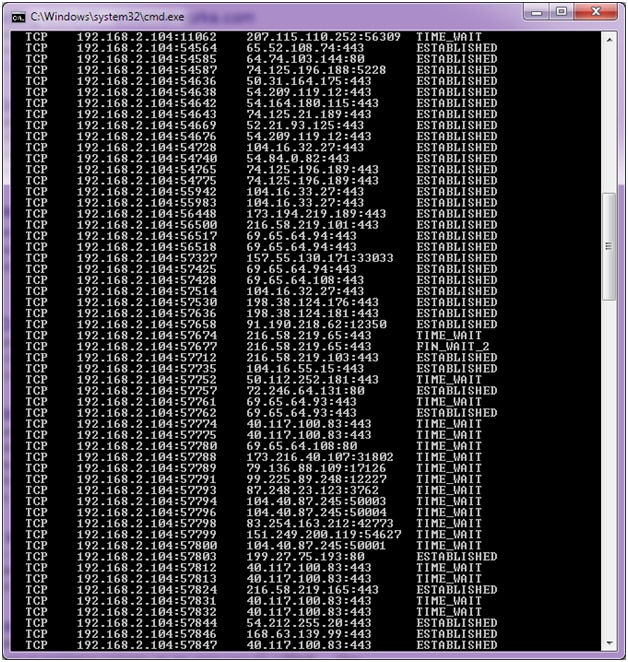
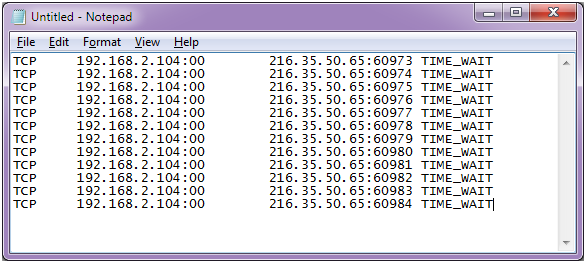
Lf_dirwatch = “300.” when you enter the following command, your server will display a list of ips connected to your server.
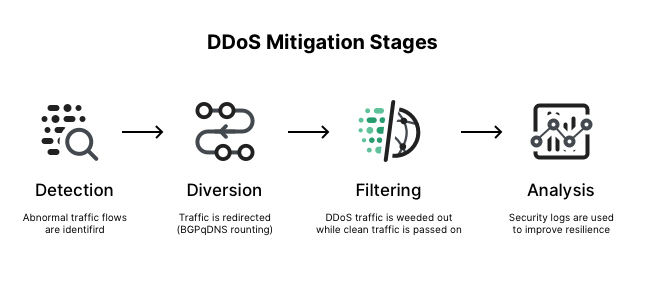
How to detect a ddos. Once you know how a ddos attack works, you can use. You can set lfd to detect suspicious directories: In the case of a ddos attack, the.
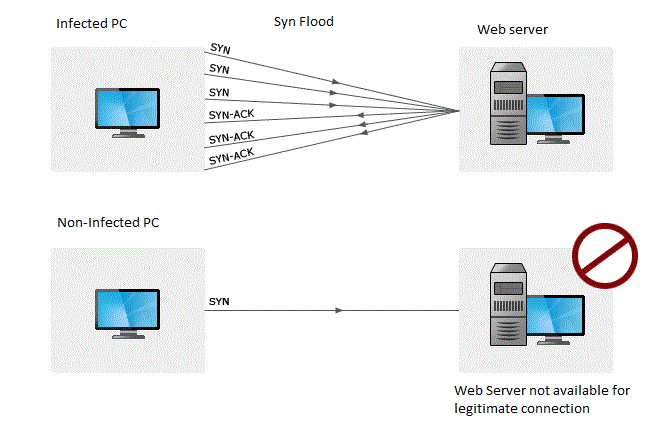
Dns request and dns response. However, a recent disproportionate spike in. Dns uses two types of packets:
This will generate standard output. While there’s no one way to detect a ddos attack, there are a few signs your network is under assault: You see a surge in web traffic, seemingly out of nowhere, that’s coming from the.
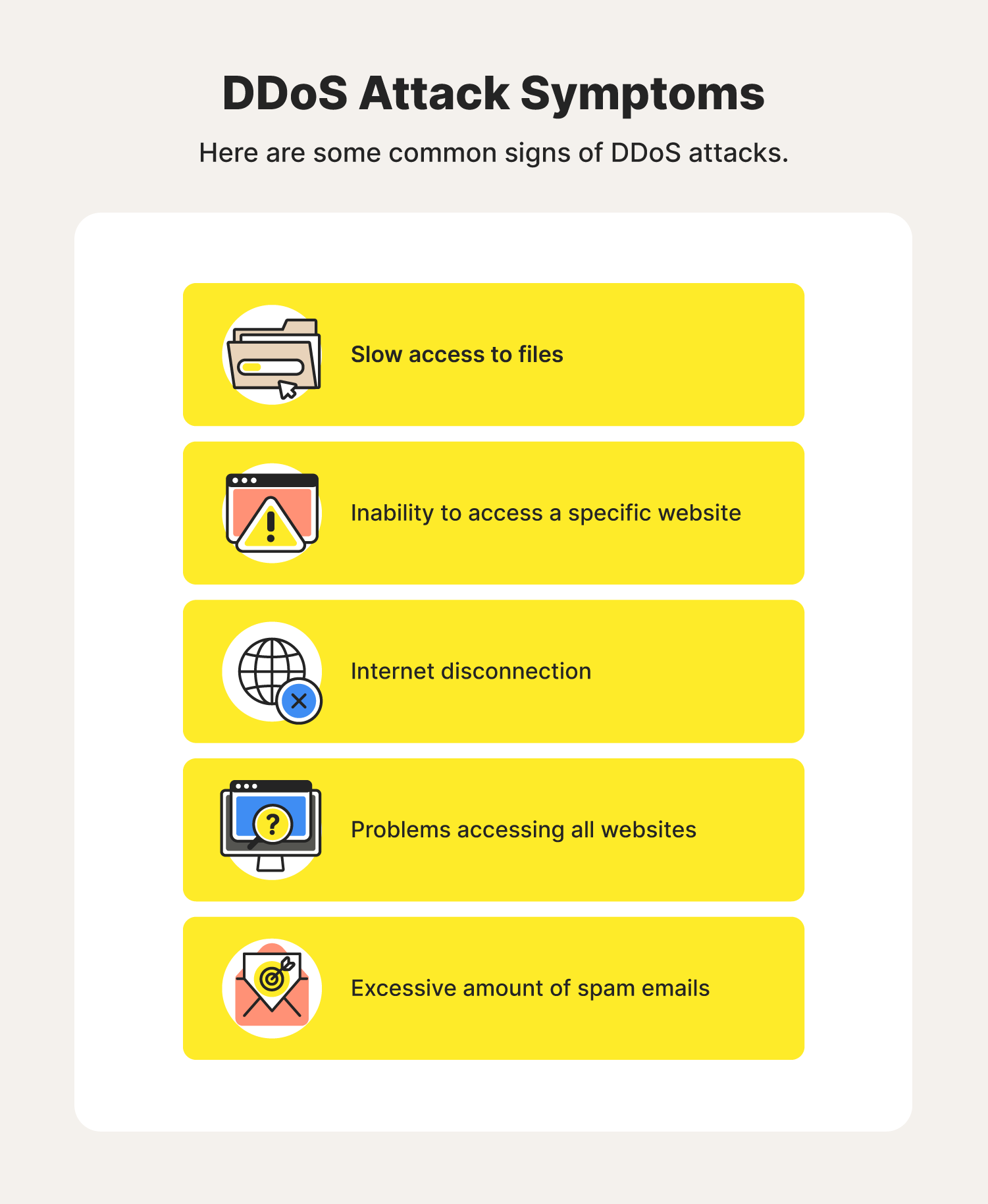
Logs contain raw data with loads of information. If you’re concerned that your server might be under ddos attack, the first thing you’ll need to do is take a look at the load on your server. 5 red flags when detecting ddos attacks.
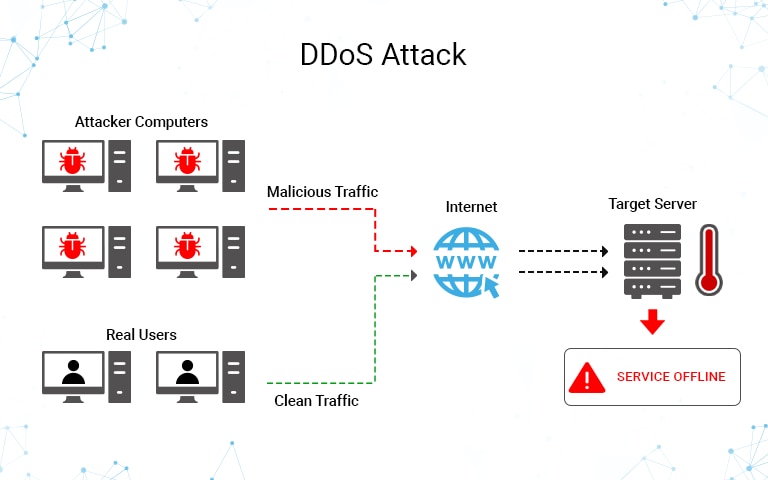
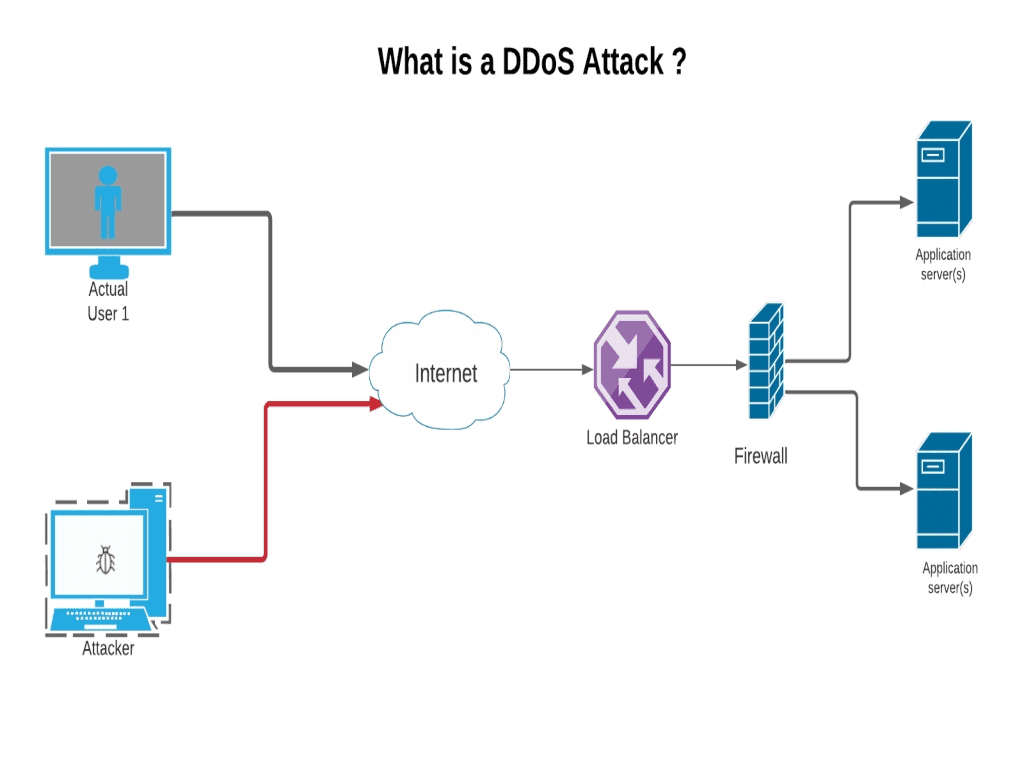
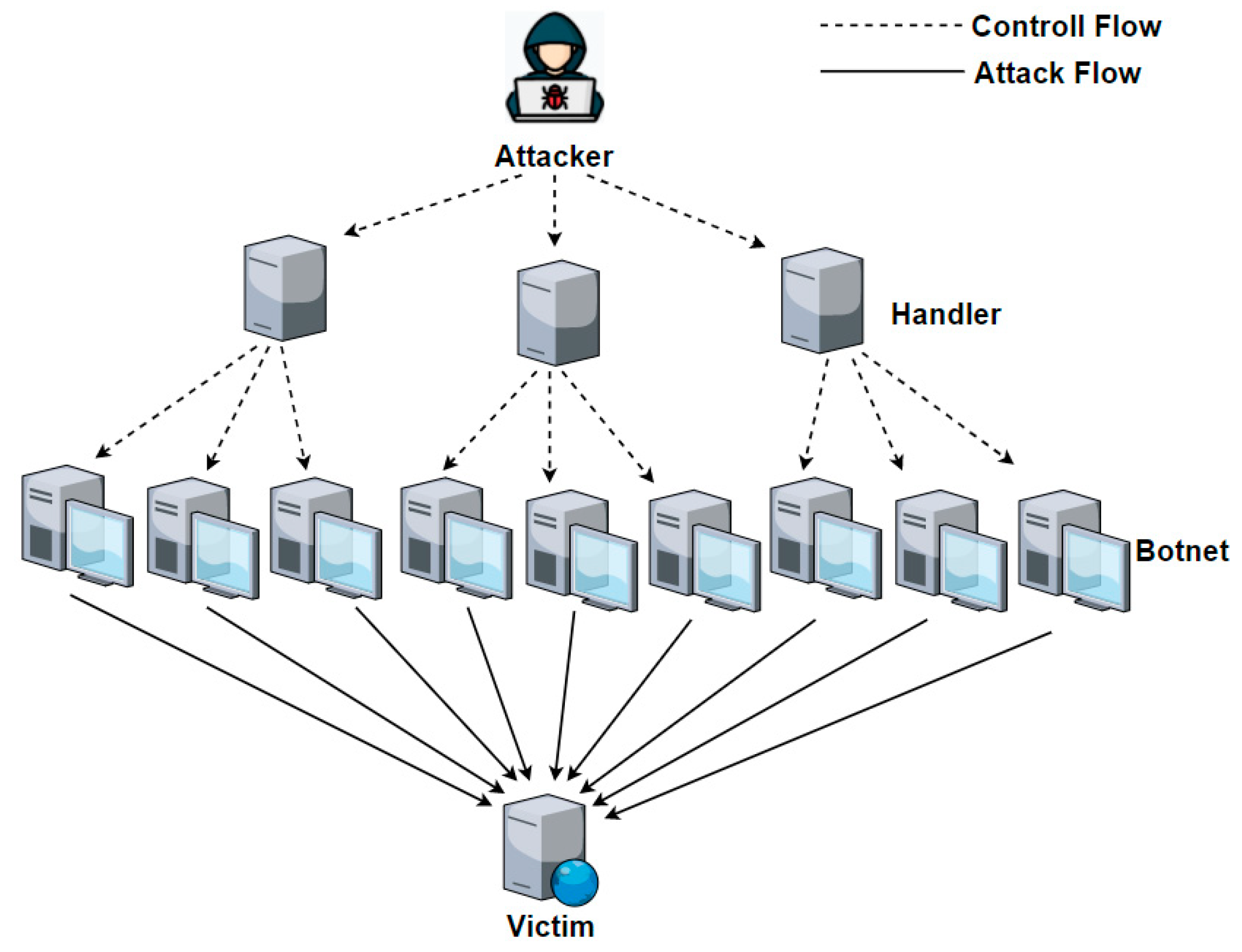
A ddos attack involves multiple connected online devices, coll. A denial of service (dos) attack is a malicious attempt to affect the availability of a targeted system, such as a website or application, to legitimate end users. A normal bandwidth chart for the last 24 hours should show a relatively constant line, with the exception of a few small spikes.
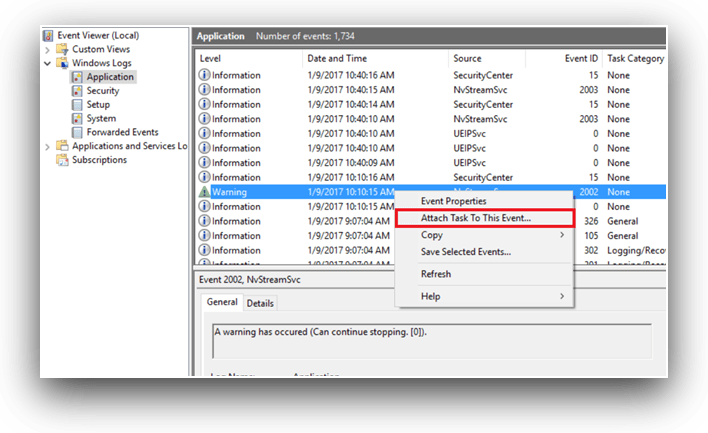
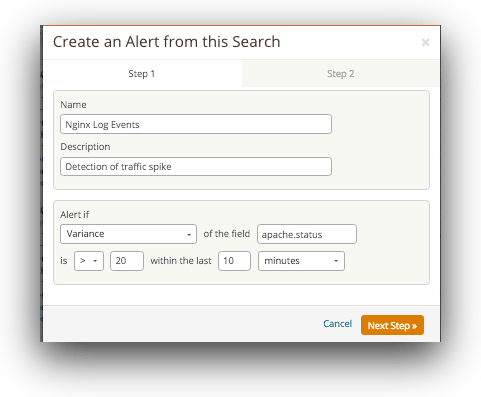
Within an hour of compromise, azure security center used microsoft’s threat intelligence to detect that the compromised subscription was likely being used as a shadow. A graphical representation of the same is an easier way to understand abnormalities and guess a potential ddos attack. Log monitoring is the best and the most effective way for quick identification of a ddos threat.




.png?width=1940&name=op%20(1).png)